Evaris Blog
All Categories Evaris Blog

11 ways to do more with software you already own
Office 365 contains a host of incredible tools and features. Granted, some of these may be suitable for your company but surely you should be using it for more than just Outlook & Word? Here is our list of the best Office 365 applications you are paying for but probably not using!

7 Reasons Why You Should Buy Refurbished Computers
Mention the word refurbished to the average man in the street and their first thoughts may be “poor quality”, “unreliable” or “broken”. Whilst for some goods and in turn the associated retailers this would be an accurate assessment, in the computing world the reality is often markedly different.

Five ways hackers could be stealing your data
It is impossible to deny that hackers are developing more complex viruses and malware techniques all the time, and while many businesses view this as the most pressing threat to their IT infrastructure, they very often overlook the dangers posed by individual members of staff.

Is the ‘demise of hardware’ an exaggeration?
For a number of years, resellers and other companies within the IT sector have been braced to contend with the changing landscape, as new developments mean that companies of all types rely less on physical solutions and migrate almost entirely to the cloud.

Everything you need to know about AI and machine learning bias
Artificial intelligence (AI) is predicted to revolutionise the future of life as we know it. Used in everything from cars to HR and recruitment processes for organisations, the technology’s potential and promise is undeniable. But along with this revolution comes a great deal of risk - biased AI.

The 5 Best Rack Servers for Small Businesses
Choosing the right server for your unique business needs is a considerable challenge faced by organisations in any industry. Finding the perfect solution for your current requirements - and one that will support any future expansion - can be particularly difficult. However, we’re on hand to assist.

Has support for your HPE Storage been discontinued?
HP are discontinuing and withdrawing engineering support for their fourth generation of HPE MSA 1040, 2040 and 2042 Storage arrays. As of 31 January 2018 these product lines will be discontinued and on 30 April 2023 all engineering & HPE support will be removed for this product line.

Three ways to encourage employee buy-in for digital transformation
Many businesses operating across all industries are currently in the midst of a digital transformation, resulting in the overhaul and enhancement of both back-end operations and customer-facing strategies through the use of technology.

How will the Internet of Things affect businesses in 2019 and beyond?
Heading into 2019, most corporate leaders are likely to have at least a basic awareness of the Internet of Things (IoT) concept, and an understanding of the major changes this high-profile tech trend is set to have on the business world.

The top five business IT trends to look out for in 2019
As we enter the final month of 2018, many business leaders will be taking stock of the significant changes that have affected the enterprise IT landscape over the last year - as well as looking forward to the continued evolution that awaits in the year ahead.

Is your business using the cloud more than you realise?
At Evaris, we speak to small business owners on a daily basis, so we think we know them pretty well. One of the things we notice time and time again is that many SME owners seem fairly reluctant to migrate their IT network and operations to the cloud, as fears over security and a lack of knowledge in this area continue to put them off.

Some of the most common threats to your network and how to combat them
The increasing sophistication of virtual security threats being used to infiltrate company networks has resulted in businesses across the globe having to tighten their security strategies, but even the most rigid systems are rendered useless without understanding from all employees.

How to create the perfect email signature
Email is a valuable tool used daily in businesses around the world, and the way employees conduct themselves using this form of communication can leave a lasting impression. A professional email signature serves an important purpose in creating a positive image for a business or brand, so it is essential that you consider yours as more than a mere afterthought.

Top password tips for safeguarding your business’s sensitive data
The threat of hacking is growing, that much is impossible to deny. Unfortunately, IT professionals are very often fighting a losing battle when it comes to encouraging their colleagues to adopt stricter security measures when carrying out their day-to-day duties. Passwords are just one area in which employees regularly fall short of what is required.

How to carry out an IT security audit
When we say “IT security”, businesses run a mile - that just seems to be the way things work. Unfortunately, we know that, despite the heavy reliance placed upon technology in the digital age, safeguarding, protecting and developing your security efforts just seems like a step too far for a surprising number of businesses.

How IT transformation is impacting businesses
Digital transformation has had a considerable impact on the corporate world in recent years, creating new opportunities for both startup companies and established firms alike. As technology continues to become an ever-increasing aspect of our daily lives, the devices and systems we use also develop. Technology is changing at a phenomenal rate, which is leading to significant changes in our daily lives, and affecting business at the same time.

How do you build an effective Business Continuity plan?
In your busiest months have you planned for any downtime? Do you have a business continuity plan in place?
Business continuity is a proactive plan which focuses on the long term operational issues of a business. Companies put a risk management plan in place which identifies the people, processes and technology required to continue business operations in the event of any interruption.

Are bored employees posing the biggest risk to data security?
A recent poll by Centrify revealed that employees who become distracted at work are more likely to pose a security risk to the business.
The data reveals more than a third (35%) of respondents said distractions and boredom are the main causes of human error, while other causes include heavy workloads (19%), excessive policies and compliance regulations (5%), social media (5%) and password sharing (4%). Worryingly, 8% believe human error is caused by not recognising data security responsibilities in the workplace.

Office 365 and the Cloud – how can it help your business?
With the bad weather very much upon us but Office 365 can be your saviour. Many businesses will be facing the inevitable phone calls from staff members who are unable to get to work. Either because they are snowed in, the roads are too bad for the cars to drive on, or schools have closed, and they have no one to look after the kids.
The importance of secure network infrastructure
Your IT infrastructure is the backbone of your business. All hardware and software needs to work and function in order for your organisation to perform to the very best of its capabilities. But, one of the biggest threats to your network infrastructure and your business is security. You need to keep your network secure to avoid situations like the recent WannaCry cyber attack.

HPE Gen10 ProLiants - Will they live up to the hype?
In early June 2017, HPE confirmed the launch of its Generation-10 ProLiant servers, which the tech giant promised would incorporate the latest in storage and memory technology that it promised will be prepared for future versions of the technologies as they are released. With the launch of the new solution set to make waves in the tech world, we thought it best to give you the lowdown on Gen10, so read on for information on everything we know so far.

IoT security threats and how to beat them
The increasing adoption of connected devices within businesses of all sizes, known as the Internet of Things (IoT) is a hot topic at the moment, and has many tech commentators feeling rather excited. It’s no wonder really, IoT is seen by many as the starting point of the most anticipated movement of our generation - Industry 4.0 - which is set to completely revolutionise the way we work and live.
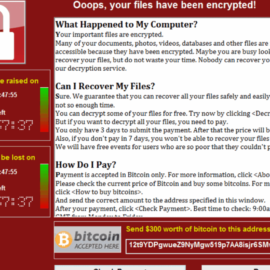
Global Ransomware Attacks – Why they were successful.
Last week’s Ransomware attacks have made global news. Though while the Ransomware attacks have been alarming, what is more interesting to us as an I.T. company is the number of aged networks still currently out there that really should have been updated.

The IT buying cycle is speeding up - what does this mean for your business?
The IT buying cycle has long since been a source of fascination for us, and other resellers, who specialise in having the knowledge to offer advice at the right moment for both new and existing customers. And for many years, elongated sales cycles have been a bugbear for resellers, as businesses have failed to make purchases in the wake of the financial crisis.

As Article 50 is triggered - what does Brexit mean for the tech industry?
The UK technology sector was an incredibly vocal supporter of Britain remaining in the European Union. In the lead-up to the referendum, large tech corporations spoke out several times in support of remaining part of the bloc, and it was undoubtedly a blow when the news of the British people voting to leave broke on the morning of 24th June.
Technology in education - what’s next?
Life in the classroom is changing, and children are increasingly using their knowledge of computers and handheld gadgets to put this experience into practice while at school. Gone are the days of sitting at a desk and working on tasks alone, the age of collaborative learning is officially upon us - and schools are increasingly looking to incorporate technology into the everyday lives of children, of course, within the constraints of ever-dwindling budgets.

Everything you need to know about load balancing
Just a few years ago, the concept of server load balancing was an expensive luxury for businesses with endless budgets, making it almost entirely out of reach for smaller companies with more modest means. However, as with many other innovations, load balancers have become increasingly accessible for small and medium-sized businesses, and products are more affordable than ever before.

Choosing a firewall - it’s no joke
There seems to be a distinct lack of urgency among a worrying number of businesses when it comes to protecting their data against cyber attacks and infiltration. Cyber security affects everyone, from at-home PC users to multi-billion pound corporations, as well as those somewhere in the middle. So, it’s time to take it seriously.

Outlook.com – some unknown keyboard short cuts!
Many of us use Outlook for emails and probably have no idea about what Outlook can do. The day to day way we use Outlook bypasses many of the simple little short cuts that Microsoft have put into it. Here’s a list of some that you may find useful when using the keyboard so you don’t have to reach out for your mouse.

Consolidating storage. A beginner’s guide
It’s an age old problem. OK, not Stone Age-old, but one that’s been with us as long as servers have been around. And the issue is the very common situation where some of your boxes are overloaded while others are functioning at 20% capacity. Indeed, 30% capacity is typical for a single use server. It’s rather like an office where a small core of staff work their fingers to the bone while the others stand around the coffee machine gossiping all day. Come to think of it ……!!

Rack, blade or tower? Which server is right for U?
This apparently never-ending recession’s taken its toll in many different ways, one being the way that a tidal wave of pent-up, frustrated investment is building up behind the damn wall of budgetary constraint. Sooner or later the damn will burst, or at least give way a little, and then you’ll be looking to refresh your servers. The question is, with what? Rack or blade server?

How long should a server last?
Servers represent a sizeable investment for many businesses so it’s no surprise that server life expectancy is an area of concern for many organisations. Given the sums of money involved, the last thing you want to do is find yourself shopping for a replacement six months down the line. There’s truth in the old adage ‘you get what you pay for’ and the key to server longevity is to allocate sufficient budget to ensure you can procure a server with the necessary feature set to support your business needs both now and in the future.
10 warning signs it's time for a server upgrade
In these austere times budgets are shrinking, belts are being tightened and IT departments are under constant pressure to do more with less. It’s therefore not surprising that many businesses are choosing to hold on to their servers as long as possible rather than looking to upgrade or replace their ageing hardware. The older a server though, the more likely it is to fail or suffer a loss of productivity.

5 good computing habits
Working on a slow, disorganized computer can be frustrating—and it happens to the best of us. This article will give you some easy-to-follow guidelines on how to keep your computer on the right track using tools in Windows 7, Windows Vista, Windows XP, and Microsoft Office 2010.

10 things you can do with your old server
It’s a question every IT manager has had to face at one time or another - what to do with a server that’s grown a little too long in the tooth? The inexorable technology march dictates that newer, faster, cheaper more powerful servers are always round the corner and the temptation is to simply get rid. After all, who wants a noisy, slow inefficient dinosaur pumping out a lot of heat and guzzling expensive power?
We are an IT Support company located just outside of Manchester.
If your business is situated in the Manchester area, we’re right on your doorstep. When an IT issue crops up that can’t be fixed remotely, we can be on-site at your premises in a matter of minutes to make repairs or fix the problem quickly so you can get back to business as usual. You’ll find our technical team friendly, helpful and professional. We’ll explain any work that needs to be carried out and run through your options without baffling you with technical jargon.
Our accreditations